Getting Started - Prepare Your Environment ## Exercise 1 - Accessing your Kubernetes Cluster ## Exercise 2 - Installing Istio ## Exercise 3 - Deploy Guestbook with Istio Proxy ## Exercise 4 - Expose the service mesh with the Istio Ingress Gateway ## Exercise 5 - Telemetry ## Exercise 6 - Traffic Management ## Exercise 7 - Security
Exercise 3 - Deploy the Guestbook app with Istio Proxy
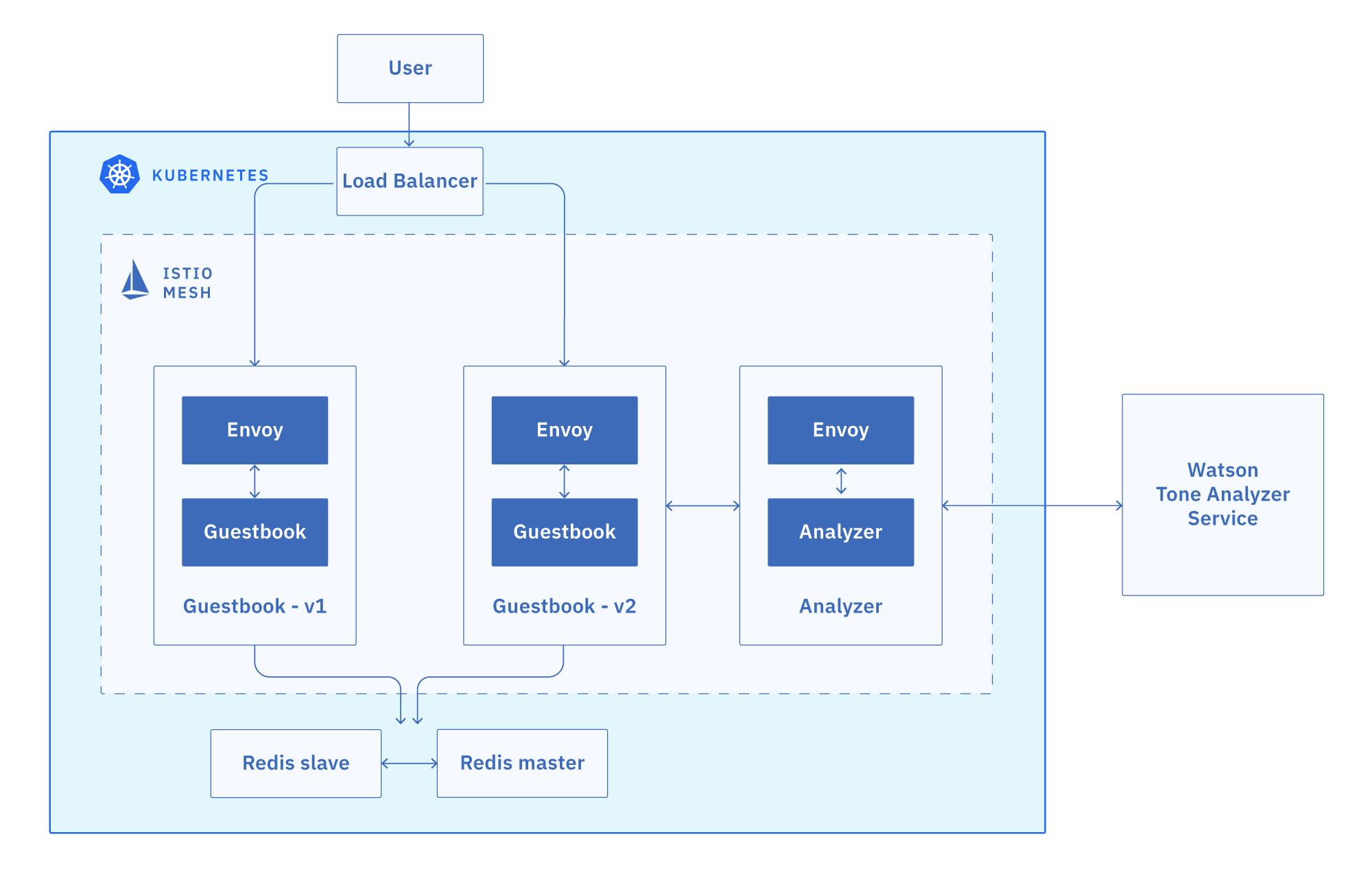
The Guestbook app is a sample app for users to leave comments. It consists of a web front end, Redis master for storage, and a replicated set of Redis slaves. We will also integrate the app with Watson Tone Analyzer which detects the sentiment in users’ comments and replies with emoticons.
Enable the automatic sidecar injection for the default namespace
In Kubernetes, a sidecar is a utility container in the pod, and its purpose is to support the main container. For Istio to work, Envoy proxies must be deployed as sidecars to each pod of the deployment. There are two ways of injecting the Istio sidecar into a pod: manually using the istioctl CLI tool or automatically using the Istio sidecar injector. In this exercise, we will use the automatic sidecar injection provided by Istio which is enabled by adding a label to a namespace.
-
Annotate the default namespace to enable automatic sidecar injection:
kubectl label namespace default istio-injection=enabled -
Validate the namespace is annotated for automatic sidecar injection:
kubectl get namespace -L istio-injectionSample output:
NAME STATUS AGE ISTIO-INJECTION default Active 271d enabled istio-system Active 5d2h ...
Create a Redis database
The Redis database is a service that you can use to persist the data of your app. The Redis database comes with a master and slave modules.
-
Create the Redis controllers and services for both the master and the slave.
kubectl create -f redis-master-deployment.yaml kubectl create -f redis-master-service.yaml kubectl create -f redis-slave-deployment.yaml kubectl create -f redis-slave-service.yaml -
Verify that the Redis controllers for the master and the slave are created.
kubectl get deploymentOutput:
NAME READY UP-TO-DATE AVAILABLE AGE redis-master 1/1 1 1 26s redis-slave 2/2 2 2 21s -
Verify that the Redis services for the master and the slave are created.
kubectl get svc | grep redisOutput:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE redis-master ClusterIP 172.21.85.39 <none> 6379/TCP 5d redis-slave ClusterIP 172.21.205.35 <none> 6379/TCP 5d -
Verify that the Redis pods for the master and the slave are up and running.
kubectl get podsOutput:
NAME READY STATUS RESTARTS AGE redis-master-4sswq 2/2 Running 0 5d redis-slave-kj8jp 2/2 Running 0 5d redis-slave-nslps 2/2 Running 0 5d
Install the Guestbook app
-
Inject the Istio Envoy sidecar into the guestbook pods, and deploy the Guestbook app on to the Kubernetes cluster. Deploy both the v1 and v2 versions of the app:
kubectl apply -f ../v1/guestbook-deployment.yaml kubectl apply -f guestbook-deployment.yamlThese commands deploy the Guestbook app on to the Kubernetes cluster. Since we enabled automation sidecar injection, these pods will also include an Envoy sidecar as they are started in the cluster. Here we have two versions of deployments, a new version (
v2) in the current directory, and a previous version (v1) in a sibling directory. They will be used in future sections to showcase the Istio traffic routing capabilities. -
Verify that the pods are up and running.
kubectl get pods | grep guestbookSample output:
NAME READY STATUS RESTARTS AGE guestbook-v1-89cd4b7c7-frscs 2/2 Running 0 5d guestbook-v2-56d98b558c-mzbxk 2/2 Running 0 5dNote that each guestbook pod has 2 containers in it. One is the guestbook container, and the other is the Envoy proxy sidecar.
-
Create the guestbook service.
kubectl create -f guestbook-service.yaml -
Verify that the service was created.
kubectl get svcOutput:
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE guestbook LoadBalancer 172.21.1.122 141.125.94.3 80:31710/TCP 93s kubernetes ClusterIP 172.21.0.1 <none> 443/TCP 7h6m redis-master ClusterIP 172.21.210.97 <none> 6379/TCP 2m46s redis-slave ClusterIP 172.21.186.161 <none> 6379/TCP 2m41s -
Open the EXTERNAL-IP of the guestbook service in your browser. You should see the Guestbook app.
Use Watson Tone Analyzer
Watson Tone Analyzer detects the tone from the words that users enter into the Guestbook app (version 2). The tone is converted to the corresponding emoticons.
Create Watson Tone Analyzer in your own account.
-
Switch to your own account by logging in again.
ibmcloud login -
From the account list, choose your own account (not the IBM account)!
-
If prompted to choose a region, select us-south.
-
Create Watson Tone Analyzer service in the
defaultresource group.ibmcloud resource service-instance-create my-tone-analyzer-service tone-analyzer lite us-south -g defaultIf the previous command errors (“No resource group found”), try ‘-g Default’ rather than ‘-g default’.
See all resource groups by running
ibmcloud resource groups. If it fails due to the region, tryeu-derather thanus-south. -
Create the service key for the Tone Analyzer service. This command should output the credentials you just created. You will need the value for apikey & url later. Save them in your environment file, too!
ibmcloud resource service-key-create tone-analyzer-key Manager --instance-name my-tone-analyzer-service -
If you need to get the service-keys later, you can use the following command:
ibmcloud resource service-key tone-analyzer-key -
Open
istio101/workshop/guestbook/v2/analyzer-deployment.yamlin an editor (nano or vi):nano analyzer-deployment.yaml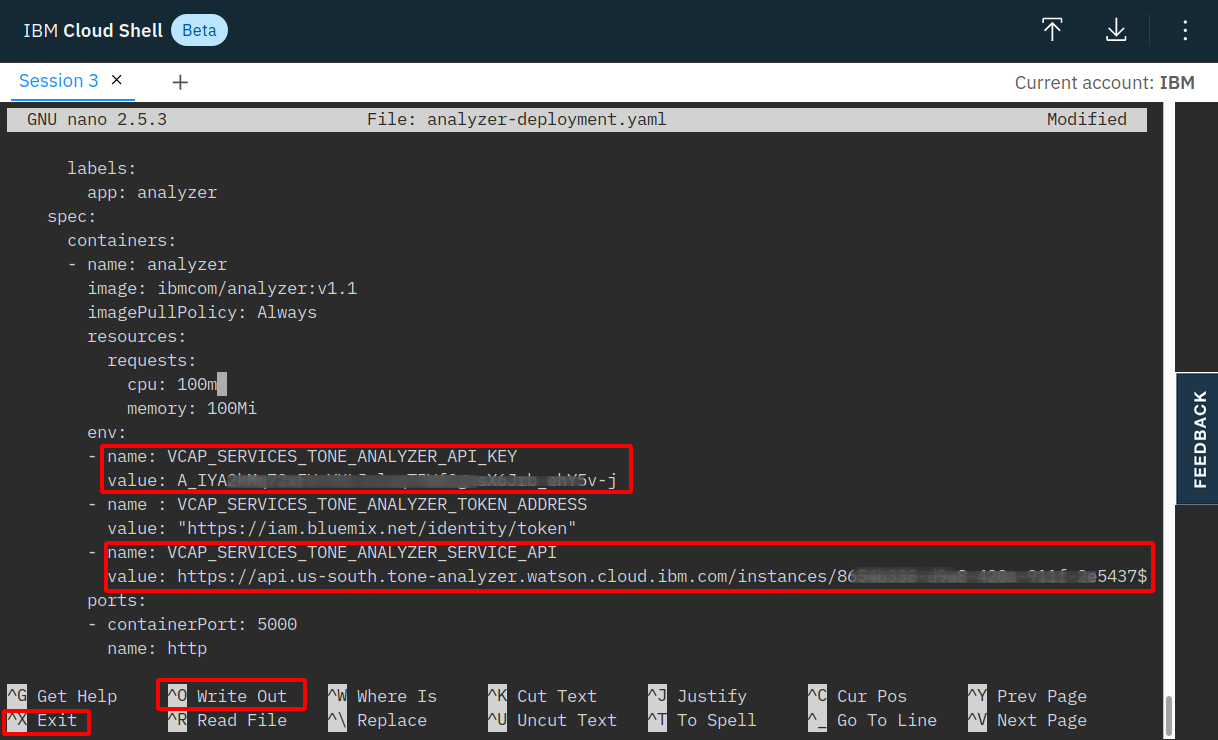
-
Find the env section near the end of the file (use cursor keys to navigate!). Replace YOUR_API_KEY with the apikey and YOUR_URL with the url, both provided earlier. With nano, save the file (Ctrl-o) and close the editor (Ctrl-x).
-
Deploy the analyzer pods and service, using the
analyzer-deployment.yamlandanalyzer-service.yamlfiles. The analyzer service talks to Watson Tone Analyzer to help analyze the tone of a message. Ensure you are still in theguestbook/v2directory.kubectl apply -f analyzer-deployment.yaml kubectl apply -f analyzer-service.yaml
Great! Your guestbook app is up and running. In Exercise 4, you’ll be able to see the app in action.